
How Cryptography Protects Your Data (& What You Can Do Today)
Lock It Up (But Don’t Throw Away The Key)
As we readied this post for publication in September 2017, Equifax announced a security breach that impacted over 145 million U.S. consumers. As I checked my social security number, I had a flashback to 2014, when a group called “Guardians of Peace” leaked information from Sony Pictures. The Sony leak included personally identifiable information of employees, salary data, copies of upcoming films, and emails containing confidential information.
Incidents like these are a good reminder of why we need to take cyber-security seriously. The Equifax breach was caused by a failure to patch a two-month-old bug, but the proper use of cryptography could have reduced the scope of what was compromised at Sony Pictures. Below you’ll find a crash course on cryptography, to explain how we keep our data secure.
Crypto-Say-WHAT?
One of the first things many people think of when it comes to security is the key to some physical object, such as a door. In the digital realm, keys are character strings used to encode data so that only those who have the correct key can decode it. We call this encryption, and it’s the foundation of digital cryptography.
Here are a few more terms that are important to the rest of this discussion:
- Plaintext – unencrypted data. An email, for example.
- Ciphertext – encrypted data. This is what the plaintext gets transformed into during encryption, and gets transformed out of during decryption. An example of this would be an email that’s in transit, using TLS encryption.
- Encryption algorithm – a mathematical formula that’s used to convert plaintext to ciphertext. This is normally used by the sender.
- Decryption algorithm – a mathematical formula that’s used to convert ciphertext to plaintext. This is normally used by the receiver.
- Key – a piece of data that, when combined with an algorithm, allows for encrypting and/or decrypting data. As we’ll see later, some types of keys should be kept a secret while others are safe to share.
There are three basic types of cryptography:
- Symmetric Cryptography
- Asymmetric Cryptography
- One-Way Hashes
Symmetric Cryptography
With symmetric cryptography, a shared key is used to both encrypt and decrypt a message. The physical key to your front door is a real-world example of this. You use the same key to both lock and unlock the door.
This same principle gets applied to software. Here’s the high-level logic that’s followed by a sender to encrypt data using symmetric cryptography:
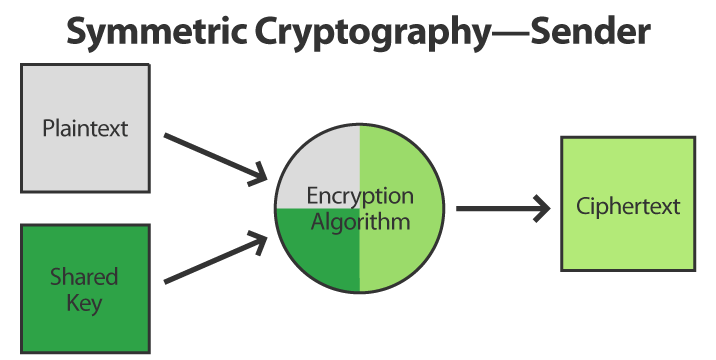
The sender combines the plaintext, secret key, and encryption algorithm to construct the ciphertext, which can then be transmitted onto the recipient.
When the recipient receives the ciphertext, it applies a similar process to convert it back into plaintext:
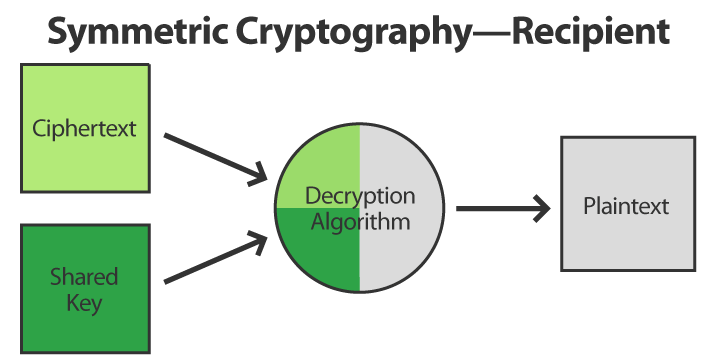
Symmetric cryptography is fast and simple (well, simple for cryptography anyway!), but has a couple of downsides:
- Since both the sender and receiver need to use the same key, secure key exchange is an issue. How can you share a new key with another party confidentially? There are solutions like exchanging keys offline or running complex algorithms, but they don’t scale well.
- They don’t provide for nonrepudiation. Nonrepudiation both proves that the sender is who they say that are, and prevents the sender from claiming not to have sent the message.
Asymmetric Cryptography
Asymmetric cryptography addresses both of symmetric cryptography’s weaknesses by replacing the shared key system with public/private key pairs. The public and private keys have a mathematical relationship that allows only the private key to decrypt information encrypted by its public key, and only the public key to decrypt information encrypted by its private key. The public key cannot decrypt data that it encrypted, nor can the private key decrypt data that it encrypted.
Here’s the high-level logic that’s followed by a sender to encrypt data using asymmetric cryptography:
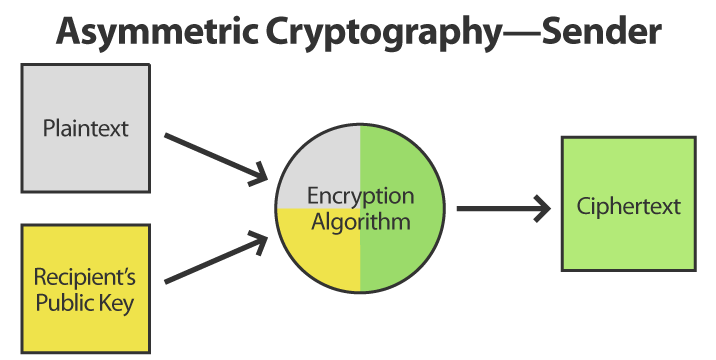
When the recipient receives the ciphertext, it applies a similar process to convert it back into plaintext:
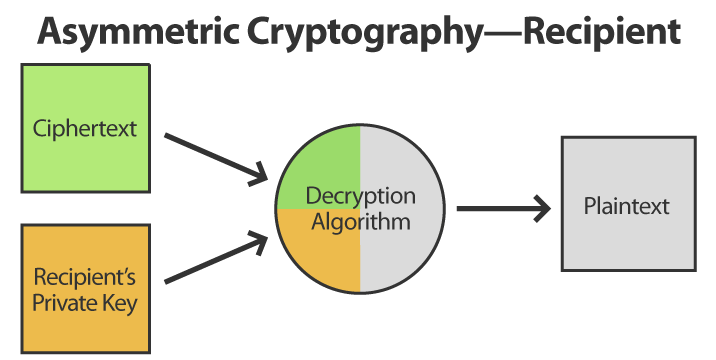
Asymmetric cryptography addresses the key exchange issue because public keys can be freely distributed. (For example, when you point your web browser to Amazon.com, Amazon sends you their public key without reservation because they’re the only party who can decrypt data encrypted with their public key.) Asymmetric cryptography also addresses the nonrepudiation issue, because everyone can have their own private key, which they keep private.
Asymmetric cryptography has one downside, however; it’s incredibly slow. It takes on the order of 1,000 times as many CPU resources to encrypt a given amount of data as symmetric cryptography.
One-Way Hashes
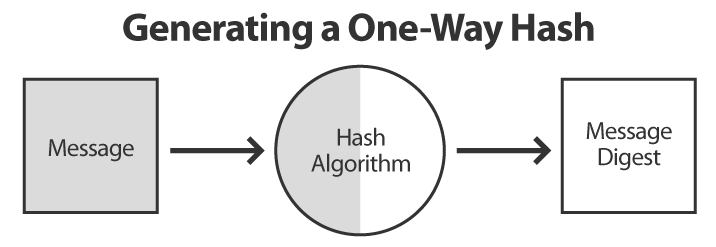
A one-way hash is an algorithm that takes a variable-length message and converts into a fixed-length message digest. For example, the SHA-256 algorithm produces a 256-bit digest, like “e9de249b7c36a4e665d65660ebeac015a6395ff2478e0a4dd42588fe5759dc28” regardless of how long the message is.
You can think of the message digest as being like a complex checksum. By storing the message digest produced by a one-way hash, you have a convenient way of verifying that the original data has not changed. All you need to do is re-run the hash algorithm and compare the new message digest to the saved message digest. If the two match, then you can be reasonably certain that the original message has not been modified.
The Sum is Greater Than the Parts
Symmetric cryptography, asymmetric cryptography, and one-way hashes can be combined to accomplish goals that couldn’t be accomplished by one in isolation. They can also be used together to emphasize their individual strengths and de-emphasize their weaknesses.
For example, symmetric and asymmetric cryptography have opposing strengths and weaknesses:
- Symmetric cryptography is fast but does not have native support for secure key exchange or nonrepudiation.
- Asymmetric cryptography provides for secure key exchange and nonrepudiation but is slow.
TLS encrypts data as it’s transmitted across a network by combining the strengths of symmetric and asymmetric cryptography.
DKIM combines one-way hashing with asymmetric cryptography to digitally sign emails. These digital signatures are used to provide nonrepudiation more efficiently than encrypting the entire email with the sender’s private key.
Encrypting Email with TLS
Email, as it was originally designed, offered no native encryption. That’s still the case for some email today, but the portion that remains unencrypted is steadily falling. According to Google, 87% of email sent by Gmail customers, and 85% of email received by Gmail customers is encrypted in transit.
TLS or Transport Layer Security (sometimes called SSL) is the cryptographic protocol that’s most commonly used for encrypting email in transit. GreenArrow can encrypt incoming and outgoing mail using TLS. (Check out our TLS Encryption for SMTP documentation page for details on how to enable and configure it.)
GreenArrow can also use TLS to encrypt a couple of additional types of traffic:
- GreenArrow’s web interface can be accessed via both HTTP and HTTPS. The HTTP Server page in our documentation describes TLS-related configuration settings, and the URL Domains page shows how to toggle click-and-open tracking links between using HTTP and HTTPS.
- GreenArrow Studio’s FTP server, which can be used for uploading lists of subscribers to either mailing lists or suppression lists, can also encrypt its transmissions using TLS.
How TLS Works
If anyone ever asks you whether TLS uses symmetric or asymmetric cryptography, the answer is “yes.” TLS uses asymmetric cryptography to negotiate a session key, then uses that key with symmetric cryptography to provide for fast encryption and decryption.
Here’s an example of how that works in an email (the same basic concept applies to TLS’ use in HTTPS or FTP):
- The client retrieves the server’s public key.
- The client generates a random session key, then uses the server’s public key to encrypt the session key before transmitting it to the server.
- The server uses its private key to decrypt the session key.
- The client and server use symmetric cryptography to encrypt the rest of their communications using the shared session key.
This procedure is a little different if the client also has a public/private key pair, but the general concept remains the same. Asymmetric cryptography is used to share a symmetric key, after which symmetric cryptography takes over.
Note that in the above example, the mail client could be—and often is—an email server that is delivering email to another server. For example, a GreenArrow server could deliver an email to a Gmail server using this process.
If you really want to geek out, check out RFC 5246, which describes TLS in much more detail.
Digitally Signing Email with DKIM
GreenArrow uses DKIM (DomainKeys Identified Mail) to attach digital signatures to the emails that it sends. These digital signatures provide nonrepudiation, which, if you’ve forgotten, proves that the sender is who they say that are.
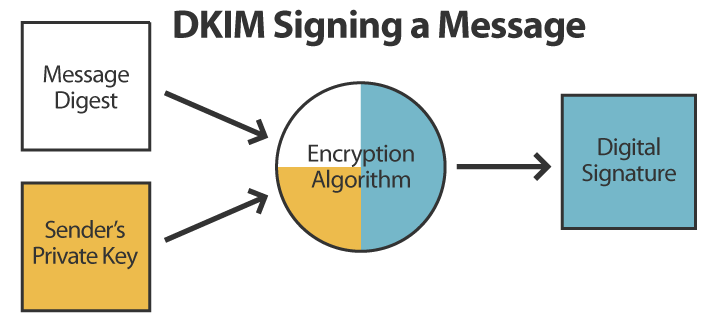
The sender creates a DKIM signature by first generating a message digest using a one-way hash. That message digest is then combined with asymmetric cryptography to produce a digital signature, which is attached to the message:
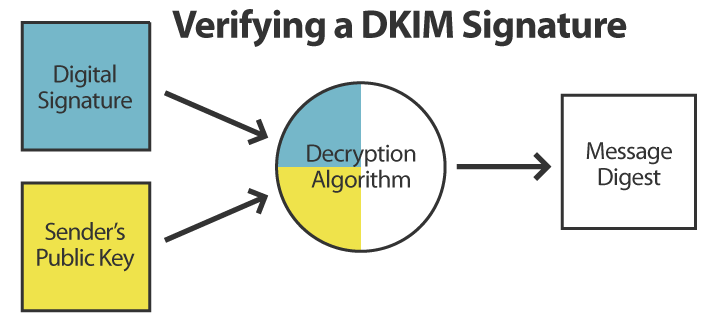
When the recipient receives the email, they both calculate a message digest, using the same process as the sender, and decrypt the DKIM signature. If the decrypted signature and message digest match, then the recipient knows that the sender is who they claim to be and that the message was not spoofed or altered in transit:
Putting Cryptography to Work
Is your head spinning? If so, don’t worry—cryptography is a complex subject. Fortunately, it’s also one that you don’t need to be an expert on to benefit from, as long as you’re using the right software in the right way.
The best way to be sure your security measures are up to snuff is to contact your provider, who will likely (read: hopefully) have options similar to the list below. If you’re a GreenArrow customer, then here are a few starting points to putting cryptography to work today:
- Configure TLS-encrypted email transmissions
- Configure DKIM to digitally sign emails
- Configure GreenArrow’s webserver to use HTTPS
- Use HTTPS instead of HTTP for click and open tracking
- Configure your FTP client to use TLS. GreenArrow’s FTP server supports TLS out of the box.
As always, we’re happy to take your plaintext or ciphertext questions. Or you can request a demo to learn more.
The Do’s & Don’ts of Naming Your IP Addresses
What’s in a Name? As humans, we love to name things: children, pets, streets, mountains, rivers, oceans, deserts, and IP…
Email Domains and Deliverability: How Setup Affects Your Sending
Hammering Out Which Domain To Use When sending email, domains are a crucial part of how people remember and experience…